Our Customers
Highlight
- 2013/07 Billows Technology was founded
- 2014/01 Became AT &T AlienVault's distributor
- 2014/08 Developed our own product “Billows LogMaster” and received SBIR grant and patent from Taipei City Government
- 2015/03 Billows participated in Taipei SBIR Achievement Ceremony
- 2016/01 Billows developed “Billows Security monitoring platform” and received SBIR grant from Ministry of Economic Affairs
- 2016/07 Billows won the NTUT Highlight Enterprise Awards of 2016
- 2018/02 Billows signed an MOU with Institute for Information Industry to collaborate with MSSP's development project
- 2018/06 Billows became AlienVault MSSP partner
- 2018/06 Became TWCERT/CC Partner & Signed an MOU to exchange threat Intelligence in 2018
- 2018/07 Received Certificate of Registration as a Technological Service Organization from Industrial Development Bureau
- 2019/09 Billows qualified as a Critical Information Infrastructure Protection testing Security vendor of Industrial Bureau of the Ministry of Economic Affairs
WHAT is our service?
Our platform provides intelligence-driven proactive defense, combining AT&T's threat intelligence, TeamT5's endpoint threat forensic analysis, and Acalvio deception technology are used to observe the attack trajectory and patterns for correlation analysis. When incidents occur, relevant information can be quickly shared for defense effectively, reducing victim cases. Moreover, the exchange of intelligence and assistance in notifications of cybersecurity incidents with Taiwan ISAC can more appropriately assist enterprises in cybersecurity defense.

WHO can use it?
Education, Government, Financial institutions, Telecommunications, and other companies and units that need to automate audits, personal data, and security.
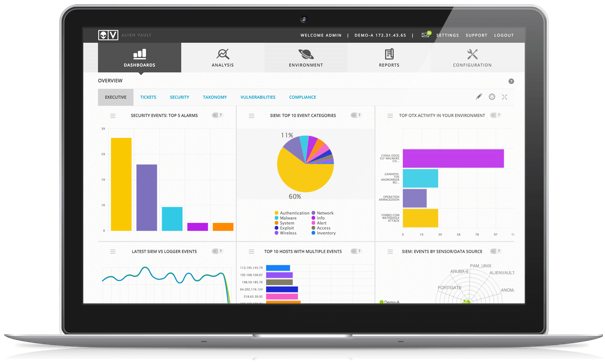
Alienvault USM
AT & T Cybersecurity's AlienVault USM is an all-in-one platform. Unlike traditional SIEM or security point products. The USM Appliance platform provides five security essential s in a single console, giving you everything you need to manage both compliance and threats. Including:
- Asset discovery,
- Vulnerability assessment,
- Intrusion detection
- Behavioral monitoring
- SIEM
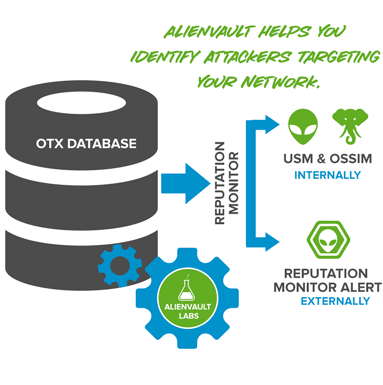
The main capability of USM comes from Open Threat Exchange(OTX). The world's largest open threat intelligence community that enables collaborative defense with actionable, community-powered threat data. OTX has gathered more than 80,000 users from 140 countries around the world. Through the platform, more than 19 million potential threats are shared daily. The USM is updated every 15 minutes and audited OTX information, so it can detect almost all kinds of real-time threats flowing around the world.
In addition, AT & T joins the Global Telco Security Alliance consisting of Softbank, Etisalat, Singtel, and Telefónica.
Alliance combines resources and capabilities of telecom operators to help protect all types of businesses from the growing threat of sophisticated cyber-attacks.
The inclusion of AT&T heightens the Alliance's ability to share insights and best practices for customers globally by harnessing the expertise of more than 6,000 security experts and a global network of more than 28 Security Operations Centers. Combined, the members of the Alliance now cover more than 1.2 billion customers in more than 60 countries across Asia-Pacific, Europe, the Middle East and the Americas.
Threat Detection
Detect malicious traffic on your network
- Network IDS
- Host IDS
- File Integrity Monitoring (FIM)
Asset Discovery
Find all assets on your network before a bad actor does
- Active Network Scanning
- Passive Network Monitoring
- Asset Inventory
Vulnerability Assessment
Identify systems on your network that are vulnerable to exploits
- Network Vulnerability Testing
- Continuous Vulnerability Monitoring
| Features: | AlienVault USM | Traditional SIEM |
|---|---|---|
| Management: | ||
| Log Management |

|

|
| Event Management |

|

|
| Event Correlation |

|

|
| Reporting |

|

|
| Trouble Ticketing | Built-In | $$
(3rd-party product that requires integration) |
| Security Monitoring Technologies: | ||
| Asset Discovery | Built-In | $$
(3rd-party product that requires integration) |
| Network IDS | Built-In | $$
(3rd-party product that requires integration) |
| Host IDS | Built-In | $$
(3rd-party product that requires integration) |
| Netflow | Built-In | $$
(3rd-party product that requires integration) |
| Full Packet Capture | Built-In | $$
(3rd-party product that requires integration) |
| File Integrity Monitoring | Built-In | $$
(3rd-party product that requires integration) |
| Vulnerability Assessment | Built-In | $$
(3rd-party product that requires integration) |
| Additional Capabilities: | ||
| Continuous Threat Intelligence | Built-In | Not Available |
| Unified Management Console for security monitoring technologies | Built-In | Not Available |
Show Case
-
 Case 1
Case 1Internal Server connected to malicious website
- Related Devices:Checkpoint Firewall(Log) & AlienLab Threat Intelligence System
- Scenarios:
- The internal server is suspected of being installed with a backdoor and sending data to an external malicious website.
- When the internal server performs general web browsing, there may be an advertisement page embedded in the malicious link.
- Response:
- Confirm the external malicious website whether it's still dangerous
- Check if the internal server is implanted with malware and clean it
- Host forensic of endpoint detection for the related hosts
-
 Case 2
Case 2The Sender is from a malicious IP
- Related Devices:Checkpoint Firewall(Log) & AlienLab Threat Intelligence System
- Scenarios:
- Suspected external malicious server was sending mails to internal server
- Response:
- Confirm the internal server whether has a mail service
- Tracking the external sending server whether is abnormal
- Confirm whether the email is sent successfully, and notify the recipient to check if the email is abnormal or delete it directly.
- If check it's a malicious mail or the mail is already open, proceed clearing the malicious software and evaluated for possible damage.
-
 Case 3
Case 3Webpage Attack
- Related Devices:Data packet and AlienLab vulnerability Scanning database
- Scenarios:
- The web server is being attack by a hacker, for example
- Execution instruction
- Stealing passwords
- Stealing database data
- The web server is being attack by a hacker, for example
-
Response:
- Confirm that the web attack was whether successful and evaluate the damage that may be caused
- Immediately reinforce all webpages' vulnerability and re-execute vulnerability scans
- Host forensic of endpoint detection for the related hosts
-
 Case 4
Case 4Blocking Service Attack
- Related Data packet
-
Scenarios:
- Suffering from hackers to perform UDP Flooding attacks
-
Response:
- Evaluate damage that may be caused by blocking service attacks
- If necessary, include the attack IP in the firewall on a short-term blocking list
-
 Case 5
Case 5Network Scanning Attack
- Related Device:Intrusive Prevention Device Log
-
Scenarios:
- Scenarios
-
Response:
- Confirm the domain query request from the server is whether legal
- If necessary, include the attack IP in the firewall on a short-term blocking list
-
 Case 6
Case 6Brutal attack of password cracking
- elated Device:Sever System Log and AlienLab NIDS
-
Scenarios:
- he file transfer service opened by the web server suffers intensive attempts to log in in a short period of time.
-
Response:
- Confirm whether the attempted account is a valid account and the password has been guessed or not.
- Require customers to set more complicated passwords and change them regularly
- Limit the IP of each account that can be connected if necessary.
Log Master

Billows LogMaster allows collecting, compressing and saving large volumes of raw logs. It also allows for integration with other reporting software to maximize visibility and allow effective visualization of internal information. Additionally, users can also automatically forward security logs to their threat analysis platform based on their custom cyber security analysis needs. LogMaster offers the following capabilities.
Log Storage: collecting and normalizing logs while performing long-term log storage and non-repudiation verification
Threat analysis: Integrating analysis within inbuilt threat modules so as to detect abnormal events
Packet storage: automatically saving packets when a specific security incident occurs, preserving the integrity of digital forensics
Quick response: provisioning of an automated response mechanism that effectively shortens response time and automatically generates the required event messages, simplifying and shortening incident response steps.
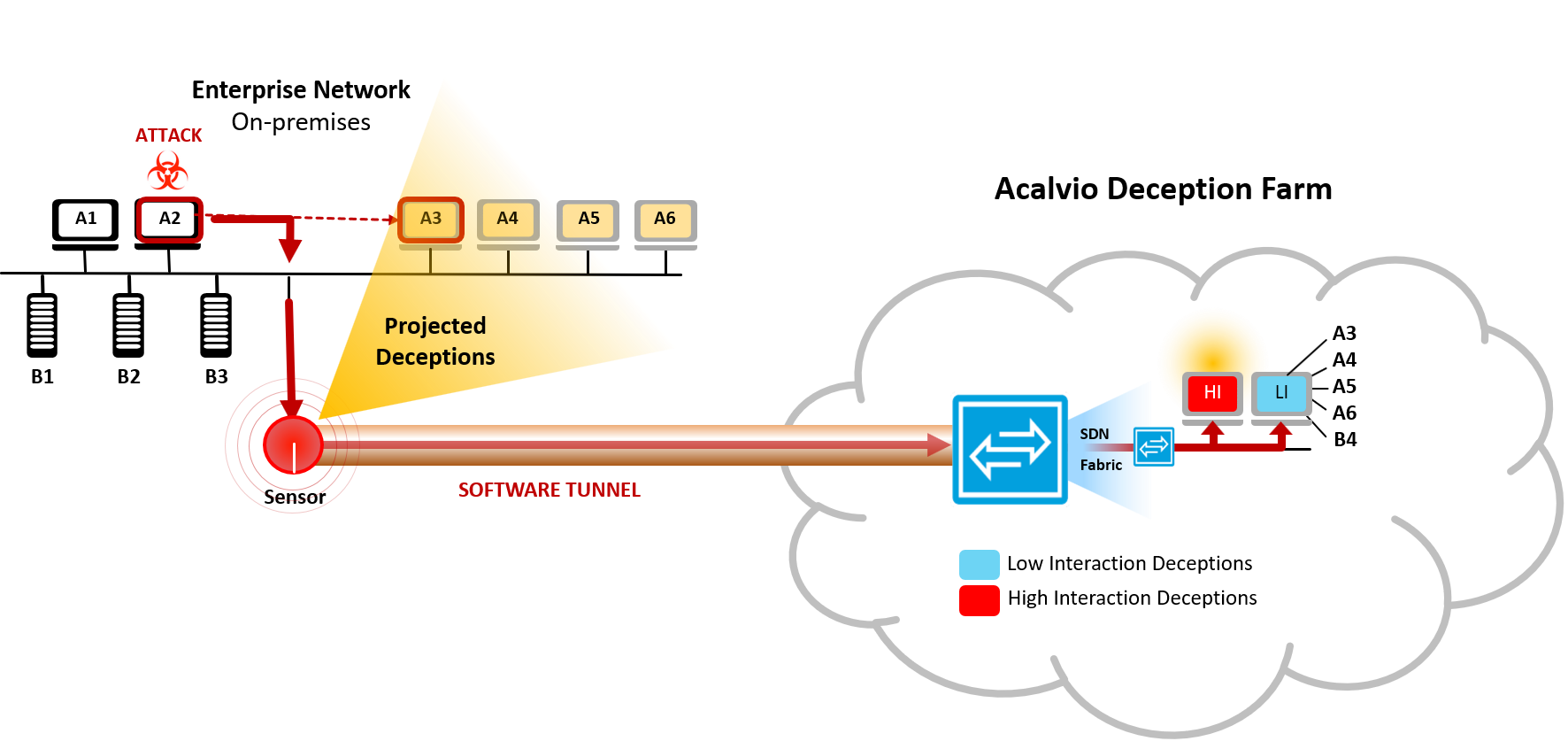
Acalvio
Acalvio ShadowPlex was highly effective in identifying, at high accuracy, malicious activity within the internal networks and detecting related east-west movement and reconnaissance. Acalvio ShadowPlex proved to have the sensitivity and accuracy to detect this sophisticated type of attack and then to alert the SOC team to it promptly. ShadowPlex detected the cyberattacker's activity early, at high integrity, and did not require any signature nor endpoint agent.
A few of the technology advantages within ShadowPlex that helped identify the incident were:
- The signature-less approach adopted by ShadowPlex helps enterprises detect even unknown versions of malware. Acalvio has found from earlier similar engagements that malware infections are sometimes undetected either because the AV protection tool could not be installed for various operational reasons or when AV protection failed to identify completely new strains of malware. The ShadowPlex solution has been proved to be effective even in such scenarios as ShadowPlex does not rely on signature of the malware for detection.
- ShadowPlex environment effectively deployed believable deceptions. Believability and attractiveness of Deceptions are extremely important for a production deception deployment that ensures attacks happen against the deployed deceptions.
- The high-fidelity incidents that were reported ensured that the right incident was captured and the enterprise was protected.
Contact us
-
Office12F., No 29-1, Sinsheng N. Rd., Jhongshan Dist., Taipei City 104, Taiwan (R.O.C)
-
Tel+886-2-2562-3952
-
Fax+886-2-2536-3763
-
Line@vri4754n
-
Email